Hundreds of sites have been effectively protected by detection technologies worldwide.
Perimeter intrusion detection system wiki.
Get a good pids system is a phrase that echoes seemingly more and more across the world.
Numerous customers once thought more traditional pids were outside their budget or unable to protect their distinctive needs.
Perimeter intrusion detection system considerations.
This document provides guidance on the specification selection usage and maintenance of the four main categories of pids.
This free standing pids works by constantly monitoring fields of vision for changes in movement to suggest an intruder is present.
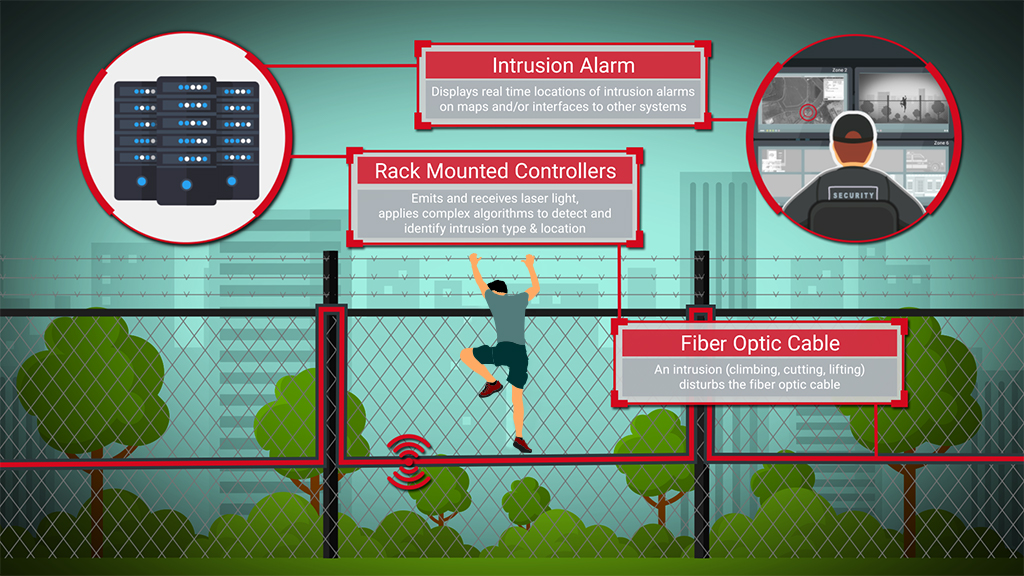
Perimeter intrusion detection system pids is designed to protect assets within a perimeter by detecting intruders attempting to gain access and blocking such access using the control station.
Facilities with perimeter detection in place range from remote petrochemical or cellular sites to vehicle.
Cctv with motion detection is one of the most well known visual perimeter intrusion detection systems on the market.
A perimeter intrusion detection system pids is a device or sensor that detects the presence of an intruder attempting to breach the physical perimeter of a property building or other secured area a pids is typically deployed as part of an overall security system and is often found in high security environments such as correctional facilities airports military bases and nuclear plants.
An intrusion detection system ids is a device or software application that monitors a network or systems for malicious activity or policy violations.
Our staff can draw on 100 man years of in the design of pid solutions.
Infrastructure to effectively specify and manage perimeter intrusion detection systems pids.
Those customers no longer feel that way.
Each frame is stored in the system and is used to monitor changes sequentially.
A siem system combines outputs from multiple sources and uses alarm.
Integrated security corporation is proud to present the hydra security fence its newest perimeter intrusion detection system.
Detection technologies manufactures perimeter intrusion detection systems pids that detect climb over and break through activity along the perimeter fence or wall.
Blue star e e offers robust and reliable solutions for accurate detection of such unauthorised entry and protection of assets against these threats.
Zero false alarms perimeter intrusion detection systems pids electronic fencing and security systems.
From scrap metal yards to prisons to warehouses car parks and even ancient monuments they all need effective perimeter intrusion detection.
Perimeter intrusion detection systems pids that stop the intruders before they enter the property don t pose any health hazards can be implemented to any wall or fence design and automatically adapt to environmental changes thus allowing for zero false alarms.